Blog categories:
Optimize your day-to-day tools for increased efficiency – templates, tips, and more
There's nothing better than cruising through the workweek feeling calm and collected. It's a difficult state to achieve, especially when you're managing multiple priorities and projects. What I've found effective is leveling up the way you use your daily apps. These small changes in [...]
4 ways to support employee well-being with technology
In today's fast-paced work environments, maintaining a healthy work-life balance and prioritizing mental health has become increasingly challenging. Constant messages, emails and looming deadlines can make it difficult for employees to log off fully after work. Discover how you can use productivity tools in [...]
SharePoint Premium Governance Features
Microsoft SharePoint Premium is the evolution of the SharePoint platform, resulting from the integration of the product formerly known as Microsoft Syntex into the SharePoint fold. SharePoint Premium brings AI, automation, and added security to your content experiences, processing, and governance. This blog will [...]
Which platform should you migrate to from Meta Workplace?
You’ve heard it right: Meta is dropping its Workplace platform and discontinuing it on August 31, 2025, to focus on the AI side of their business. This may come as shocking news to the organizations currently using Workplace, leaving them scrambling to find the [...]
How to use SharePoint Premium Content Processing
According to Microsoft, about 1.6 billion documents are added daily to Microsoft 365. Today, organizations spend $46 billion per year storing and managing content, and it is estimated that by 2025, there will be more than 130 billion terabytes of content. With SharePoint Premium’s [...]
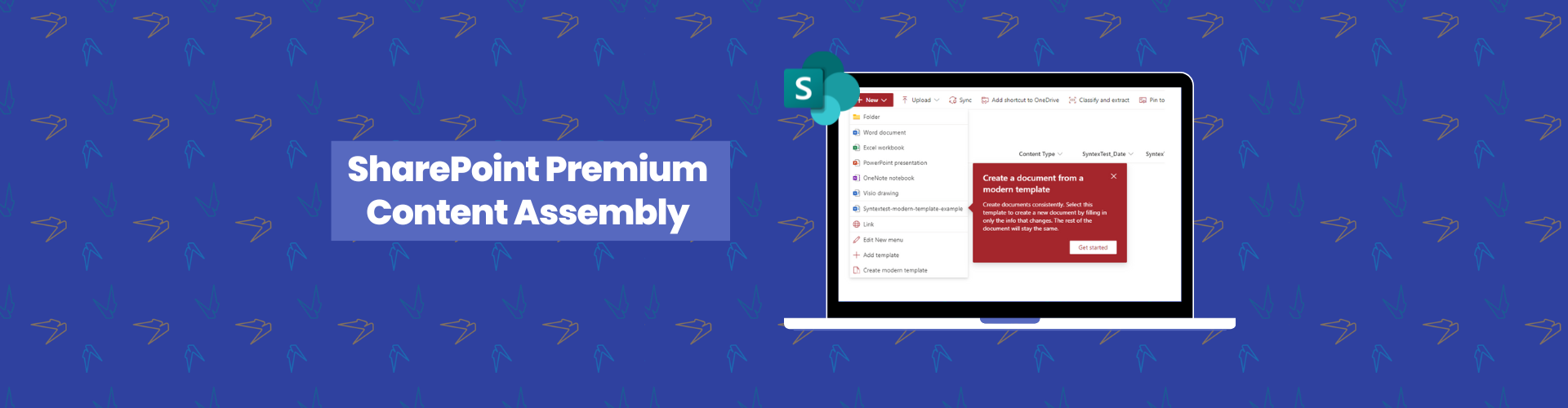
Practical use cases for SharePoint Premium Content Assembly
Looking to make your life a bit easier and reduce repetitive manual document tasks? SharePoint Premium content assembly is just what you need as a tool that streamlines document creation with AI and automation. Discover practical use cases for content assembly that you can [...]
Adding your custom fonts to the SharePoint Brand Center
Infuse your brand’s essence and personal flair into every page and site—unleash your custom fonts into SharePoint and make your digital presence as unique as your brand. Here's a detailed tutorial on how to add custom fonts in your new brand center. Once your [...]
What you need to know about Microsoft SharePoint Premium
Microsoft’s SharePoint platform has been around since 2001, which no doubt makes it older than some of its current users, but its evolution has been constant. SharePoint Premium has recently been rebranded from Microsoft Syntex, and you’re missing out if you’re not aware of [...]
How to prepare for the new SharePoint Brand Center
What is the SharePoint Brand Center The SharePoint Brand Center is Microsoft’s new centralized application for managing brand elements including colors, fonts, and additional graphical assets. Gone are the days of updating each site separately, you can now manage brands centrally. [...]
A complete guide on Microsoft Dataverse: Best practices and tips
It’s no secret that data lies at the heart of every organization's success. Efficient data management, storage, and integration are crucial for driving business agility, enhancing decision-making, and fostering innovation. That’s where Microsoft Dataverse comes in—a robust and secure data platform that empowers organizations [...]
How to prepare your data to get the best results from AI
Artificial intelligence (AI) is a powerful tool that can help your businesses automate data processing and derive value. However, the quality of the results produced by AI algorithms is only as good as the quality of the data fed into them. In other words, [...]
How to maximize your AI investment in Microsoft Copilot
You’ve heard about ChatGPT, but what about Microsoft Copilot? What if we were to tell you that Microsoft Copilot can do what ChatGPT does, but more as an AI tool embedded in your day-to-day apps, holding the potential for your organization to realize significant [...]
62 real world use cases of Copilot in Microsoft 365
Generative AI is the new frontier, and among all the emerging models, Microsoft Copilot stands out with its deep integration with the Microsoft 365 suite. Copilot enables users to get the most out of their Microsoft 365 subscriptions. Whether it's using Copilot to draft [...]
What is Microsoft AI Builder?
Interested in building an AI model tailored to your business needs but not sure where to start? Microsoft's AI Builder, part of the Microsoft Power Platform, is your all-in-one solution. This guide will walk you through using AI Builder and answer common questions, so [...]
Microsoft 365 Business Premium vs. Google Workspace Business Plus
It’s easy to be struck with decision paralysis when considering all the cloud solutions on the market. There seems to be an endless number of services and licenses available, but which one is the best fit for your organization? Committing and transitioning to a [...]
How long does it take to implement an intranet project?
When I was an internal technology strategy consultant for a very big bank, we used to joke about this kind of question a lot; the “but how long does it take to <insert your project here>” type question will always solicit the same [...]
Copilot Readiness Checklist for the Power Platform
If you haven’t been living under a rock, you have probably heard the word on the street — Copilot is in, and everyone’s trying to figure out what it is and how to use it. Among other uses, this virtual AI assistant lets you converse [...]
Getting Started with Copilot in Power Platform
Have you ever wished you could just ask someone else to do your work for you? With Microsoft 365 Copilot’s integration into the Power Platform, your wishes can become a reality. Copilot, an AI-powered assistant, can help you develop apps and build automated workflows just [...]
How to Measure Success and Define ROI for a Digital Workspace?
A digital workplace is a virtual environment that provides employees access to a combination of communication, collaboration, and knowledge management tools that help them do their jobs from anywhere, at any time. To evaluate the success of your digital workplace, you must define and measure [...]
How to Stay Productive During Winter | Beat Those Winter Blues
You wake up, grab your coffee and throw a blanket over your shoulders. You turn on your screen to tackle the day, but the cloudy weather makes it tough to focus. You feel drowsy, and ideas aren't flowing. What spell has taken hold of your [...]