Author
Danielle
Gone are the days when companies accessed and stored their resources on-premises. Now, hybrid and remote work is a reality that’s here to stay and securing data has become an urgent priority. Companies in the past functioned through their own secure on-premises network but today, that boundary is expanding with the cloud. Employees are working from any location, on any device, within or outside the organization’s network. This begs the question; do you do enough to protect your organization? If you have any doubt, consider implementing a Zero Trust security model.
The Zero Trust security model is based on the foundation that there are threats everywhere— both inside and outside your organization’s network. Simply put, you’ll treat your organization’s internal network as if it can’t be trusted. Your security model will assume that all devices trying to access your data are potential threats and, as a result, will verify each access request with caution. This is why the Zero Trust security model is one of the best ways to adapt to the modern work environment: on-site, hybrid, and remote.
The following are the guiding principles of Zero Trust that establish security measures in the organization.
- Verify explicitly: Use all information available to permit or deny authorization
- Use least privileged access: Limit user access with Just-in-Time and Just-Enough-Access, risk-based adaptive policies, and data protection.
Just-in-Time is a feature where you give a user access for a predetermined amount of time on an as-needed basis. Just-Enough-Access, as its name suggests, hinges on giving just enough access to a user through the assigning of roles.
- Assume a breach: Segment accesses, verify end-to-end encryptions, and use threat detection tools to continuously monitor the security perimeter and improve defenses.
A Zero-Trust approach is best utilized when extending throughout the entirety of your organization’s network. This allows the security model to function as integrated security, acting as your end-to-end security strategy. There are six fundamental pillars in the Zero Trust security model, and we break them down in-depth below.
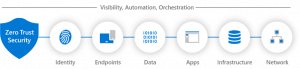
How does the Zero Trust security model secure organizations?
Secure identity
To understand how Zero Trust secures identities, you first must understand what a control plane is. A control plane is the part of a network that controls the way data is sent across the network. Identities describe people (such as user data, passwords, biometrics, etc.), services, and Internet of Things (IoT) devices. In essence, these identities act as access points to your organization’s data. This is why compromised employee credentials are more dangerous than you think. It’s more than a compromised account, you should think about it as having a compromised access point into your organization. Through Zero Trust, when an identity attempts to access data, verification of that identity is always required. Back to “never trust and always verify,” this is done to ensure that there’s nothing out of the ordinary with the identity. Now, what is considered out of the ordinary? An example of this would be a user logging in from an unusual location. This should raise concerns about a potential user identity being stolen or hacked
Secure endpoints
Naturally, in a remote or hybrid setting, you’ll have many different identities accessing organizational resources. This creates a wide range of endpoint flows, which can quickly become an issue. Why is this the case? To explain this concept, I want you to think about a house. Doors leading into a house can be vulnerabilities used by intruders to break in. The more doors there are the more options for the intruder to choose from. The same concept applies to your network. The more access points you have in your network, the more entry points there are for hackers to break into your network. That’s why it is important to ensure that each device meets the organization’s security requirements by implementing compliance measures for secure access. What’s an example of a compliance measure? An example would be an organization checking the operating system (OS) version of their device through the use of Intune before the device gains access to the network.
Secure applications
Here, “applications” refers to software that satisfies the technical management needs of a business such as customer relationship tools. Some common tools you may have heard of are SalesForce or Dynamics 365. Other examples include legacy (older applications that are outdated), on-premises, or modern Software as a Service (SaaS) applications. Zero Trust can be used to manage shadow IT, app permissions, real-time analytics, user action, configuration options, abnormal behavior such as unusual log-in times, and the blockage of unauthorized workloads
Secure data
Data should be protected within a secured boundary,: a boundary you set for your organization to keep your data safe. In cases where data leaves that boundary, protection policies should follow with the data. Classify, label, encrypt data, and restrict access based on those security attribute
Secure infrastructure
Infrastructure refers to the hardware and software components that a computer network is constructed with, namely servers. Cloud infrastructure providers include Microsoft Azure, AWS, Google Cloud and many more You can also have on-premises infrastructure, or live in a hybrid world. Ensuring that infrastructure is up to date and protected against threats is an important part of implementing Zero Trust. Just-in-Time access is enforced to harden the defense of an infrastructure and telemetry is used to detect attacks and anomalies that may be happening in real-time to ensure you are able to detect attacks, take action against risky behaviour, and take proactive measures against future threats.
Secure networks
Zero Trust advocates for you to always treat your internal network as if it can’t be trusted by verifying all access requests as if they originated from an uncontrolled network. Make sure that all network– sessions -internal and external- are encrypted. Securing and encrypting help prevent attackers from getting access across the network. Deploying real-time threat protection, end-to-end encryption, monitoring, and analytics are integral to securing a network with Zero Trust.
Visibility, automation, and orchestration
All the previous pillars work together to provide improved visibility of cyber-security threats. Each pillar provides its own relevant alerts, which then gives you the capability to manage the resulting influx of data to defend against threats and save your data from unauthorized access.
Today, organizations need a new security model that effectively adapts to the complexity of the modern environment, embraces the mobile workforce, and protects people, devices, applications, and data wherever they are located.
How to Implement Zero Trust security Model using Azure AD?
Azure Active Directory (Azure AD) is a Microsoft solution designed identity service providing single sign-on, multifactor authentication, and conditional access to guard against cyberthreats, attacks, and provide general cybersecurity governance. Here is how to get started with Zero trust with Azure AD:
Connect all users, groups, and devices to AD
Make sure to implement an authentication method for users. Set the Multifactor authentication so all identities are validated before giving access to the resources. Passwords can be eliminated in favor for use of biometrics or two-factor authentication.
Integrate all corporate applications with Azure AD
When you add applications to the enterprise application list in Azure AD, Single Sign On (SSO) will be required for all users logging in to the application. SSO is not only a convenient feature for users but also a great security measure as it prevents users from leaving traces of their credentials in multiple enterprise applications. Azure AD also supports other application authentication methods including the following:
- Integrate modern enterprise applications to connect to OAuth2.0 or SAML.
- Integrate using Azure AD Application Proxy, this can be used for Kerberos and form-based authentication applications.
- If legacy applications in your environment are published using application delivery networks or controllers, Azure AD can integrate with major controllers such as Citrix, Akamai, F5, strata, kemp, etc.
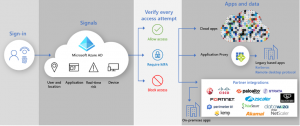
Automate provisioning to applications:
After all users’ identities are in Azure AD, now it can be used to power push those user identities into your cloud applications. This will provide a tighter identity lifecycle integration within those apps.
Get your logging and reporting in order:
After you have set up your organization Azure AD with its authentication, authorization, and provisioning, the next important step is to have a strong operational vision of the contents in your directory. This Azure AD reporting and monitoring will provide a comprehensive view and log of activities in your environment, these include sign-in events, audit events, and changes to the directory
Do you need a Zero Trust security model?
In the last few years, the working model has drastically changed and transformed into a hybrid model. The increase in cloud-based services, use of mobile devices, working remote, and bringing your own device (BYOD) into the workforce has changed the way we work. Now, work is not limited to the organization’s network boundaries. We need a modern solution to keep our organization’s information secure. Security architecture used to be confined and relied on network firewalls and virtual private networks (VPNs) to control and restrict access to the resources. However, these services are no longer sufficient.
Did you know that more than 80% of all attacks involve compromised credentials?
If your organization has the below-mentioned elements in your environment, you should consider implementing this cybersecurity model to effectively secure your organization from any breach.
- Multi-cloud, hybrid, remote, multi-identity
- Unmanaged devices
- Legacy systems
- SaaS apps
- Industry or compliance requirements (e.g. financial sector or government compliance)
You must address key threat use cases including:
- Ransomware – Involves encrypting your data and identity compromise
- Supply–chain attacks – involves unmanaged devices and privileged users working remotely
- Insider threats – especially challenging to analyze behavioural analytics for remote users
That was a lot to take in, trust us, we know. You may not know where to start, but that shouldn’t stop you from securing your organization. Let us help! Book a security consultation with us so we can help you define your organization’s security needs, secure the optimal licenses, set them up to protect your valuable data, and help you find peace of mind along the way.



















