Tighten Your Security with Microsoft 365
After a stressful day, Evan, your employee, opens his email inbox.
Another email from work, and so late? Great.
He opens the email, and it’s from your IT colleague, asking him to click the link in the email. Something about it looks a bit off… Why?
Tired and ready for bed, he clicks on the link and follows the listed instructions.
Wait a minute, is this a work email? His heart sinks, as he wonders what he just did…
Sorry to break it to you, but you and Evan are now victims of a cyber-security attack.
The reality is that even the most harmless-looking spam email can be the foundation of a ruthless cyber-security attack compromising not only the integrity of your business operations but your data as well. Employee information, business partners, and customer data are all in the hands of hackers. What a disaster. Now, that’s just a hypothetical; you still have time. With the rise in the rate of annual cyberattacks, what better time is there than now to secure your organization?
Top 5 key security features of Microsoft 365 to help secure business operations and data
Azure Active Directory Premium Plan 2
Azure active directory (Azure AD) is a cloud-based service which helps users access external and internal resources like Microsoft 365, Azure portal, SharePoint, Teams, Exchange and other third-party or Software as a service (SAAS) applications. With Azure AD premium plan 2, users can utilize the second layer of Identity Protection and Privileged Identity Management Capabilities (PIM) features along with Single Sign-On and Multi-factor Authentication.
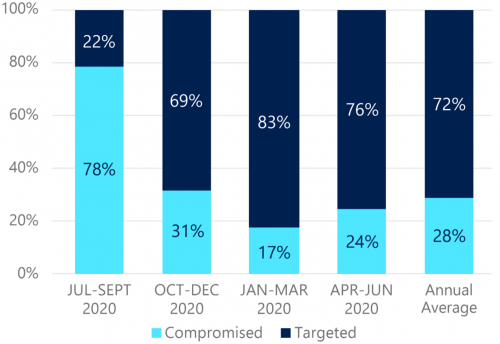
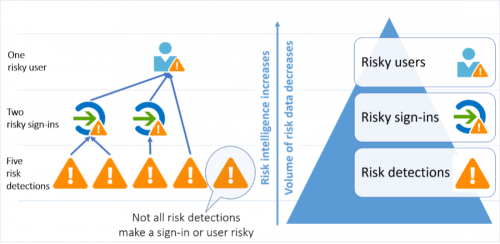
What is the Identity Protection feature you may ask? Identity Protection can identify major vulnerabilities and will respond automatically to malicious cyber-security attacks by locking critical information technology systems. Simply put, it’s like getting locked out of your phone for 30 seconds after 5 wrong attempts. Now, we recognize that every organization’s security infrastructure is different and that’s why Identity Protection also allows assigned administrators to configure these automated responses to match your organization’s security standards. These risk-detection and countermeasure features include anonymous IP address use, atypical travel, malware-linked IP address, unfamiliar sign-in properties, leaked credentials, and password spray.
Example: If the Azure active directory detects that a user is signing in from an anonymous IP address, malware linked IP, or in a case of leaked credentials, Azure will automate a security feature such as multi-factor authentication, self-service password reset or in severe cases, Azure will completely block the user until an administrator investigates the situation.
Azure Premium Plan 2 as previously mentioned also offers the PIM feature which has the capability of managing access to the tenant environment. Every organization wants to minimize the number of accesses to the Microsoft Office portal or Azure portal. Keeping this in mind, Microsoft allows the capability of controlling the user’s access based on the time and approval from an administrator to mitigate the risks of excessive, unnecessary, or misused access permissions.
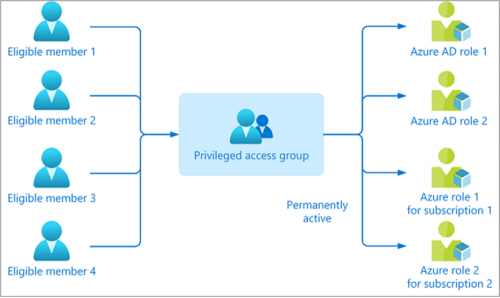
Example: Imagine there is a user that isn’t the Global administrator on the tenant but wants to change settings on the Azure portal tenant-wide. In this case, a user can request access through the Privileged Identity Management feature that is time-bound and provides justification for the request. Once the user request is approved by the administrator, the user can make the changes in the tenant with Just-in-time privileged access to Azure AD and Azure resources.
Microsoft Defender for Endpoint
Another next-level feature offered by Microsoft is called Microsoft Defender for Endpoint. For any organization that wants to implement cyber-security effectively, Defender for endpoint has a set of policies which will inform you if a user’s devices are at an elevated risk. This defender security platform is designed to help network platforms detect, investigate and respond to advanced-level cyber-security threats.
Microsoft Defender for Endpoint uses advanced techniques with the combination of endpoint behavioural sensors, cloud security analytics, and threat intelligence to ensure the protection of your end-users.
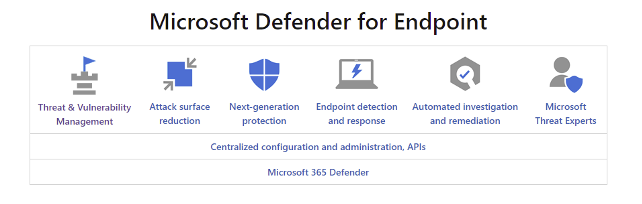
Microsoft Defender for Endpoint also integrates with various other Microsoft solutions such as Sentinel and Intune. Due to this, Microsoft defender for Endpoint can manage a variety of different types of devices including Windows 10 & later, Microsoft servers, Android, and Apple. Once a device is onboarded to Microsoft Defender for Endpoint, Administrators will have the ability to track the devices remotely without any user interference. Specifically, administrators can record alerts for spam, malicious activities and security loopholes compromising the endpoint security. A report then can be generated that includes but is not limited to security alerts, malware, web filtering, and a list of various vulnerabilities. Microsoft defender for endpoint has its own separate portal just like Azure and Intune.
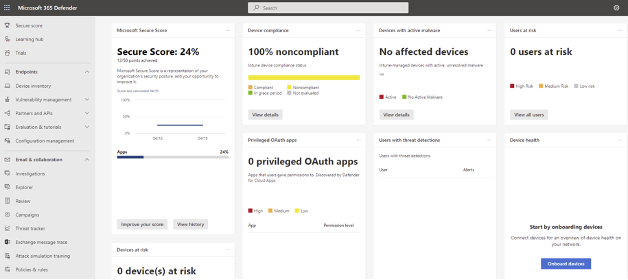
Advanced Threat Protection
Advanced Threat Protection (ATP) falls under security features that defend against hacking-based attacks on users to target sensitive data. ATP includes a package features of the device’s network security, email gateways and malware protection. ATP functions focus on three main aspects where security leaks typically occur: detection of critical cyber-security threats before they breach your systems gaining access to your data the power to defend against detected critical threats smoothly, and the ability to mitigate these threats by responding to major security incidents. This is possible through ATP due to the following features:
- Real-time visibility – Prevents threats in real-time protection rather than after the damage.
- Context functioning – Works with the context to ensure that IT teams are informed of the threats and able to respond promptly.
- Data awareness and understanding – Ability to analyze the sensitivity of data so that ATP tool will find attacks and quickly respond to them.
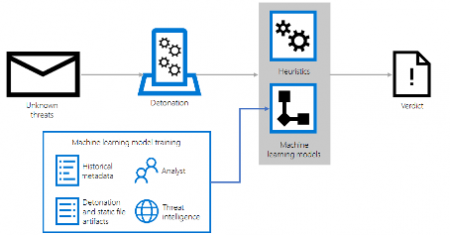
ATP also performs vulnerability assessments with the help of an attack simulation identifying all vulnerabilities and threats. This is important as real-time action attack modules help your organization in educating their users or employees on spreading cybersecurity alertness efficiently.

Information Protection and Governance
Information protection and governance with Microsoft helps organizations to protect and regain their data from where it is situated and where it is flowing. The two major aspects of this feature are Microsoft Information Protection (MIP) and Microsoft Information Governance (MIG).
Microsoft Information Protection (MIP) detects, distributes, and defends critical business content through its architecture across the organization. MIP supplies a set of tools to know your data, protect your data, and avert data loss.
Microsoft Information Governance (MIG) administers your architecture using its solutions to import, store and classify critical data so that you can keep and store what users need and remove what they do not. MIG also provides options to govern organizational data for compliance and regulatory purposes.
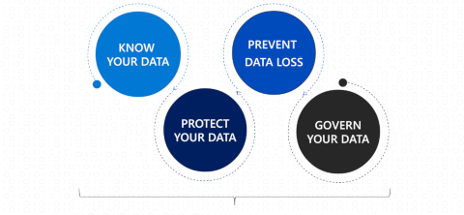
MIP and MIG come with other security options such as Data loss prevention (DLP) and Sensitivity labels. DLP is an approach to protect sensitive information and counter its inadvertent disclosure. With the DLP option administrators can identify, check, and automatically protect critical data across various other Microsoft services such as OneDrive, SharePoint, Teams, and Exchange. It also helps users learn how compliance and standards work without opposing their workflow. DLP policies secure data by enforcing the rules that consist of conditions, actions, and locations.
Example: An administrator can create a DLP policy that helps detect data that is subject to compliance standards like Health Insurance Portability and Accountability Act (HIPAA) across all SharePoint and OneDrive data.

Inside the DLP policy, one or more rules can be configured, and each rule subsists of conditions and actions. The rules inside the policy will be implemented based on their priority. For example, in the above diagram, rule one will be implemented before rule two and so on.
Following the DLP policies, sensitivity labels enable the protection of the data without interference in the productivity of work. These sensitivity labels can apply to common organizational content such as emails and documents and follow category schemes such as Personal, Public, Confidential and Highly Confidential. Arguably the most important feature of sensitivity labels is its ability to encrypt emails and documents during the data flow on the cloud.
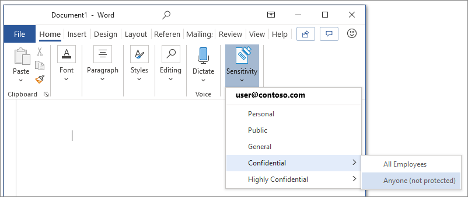
What this means is once a sensitivity label is applied to an email or document, all the configured settings for the label will be enforced on the shared content.
Microsoft Defender for Cloud apps (Microsoft Cloud App Security)
Microsoft Defender for Cloud apps is a module that supports and works smoothly with other services. It provides an added layer of security during data travel and can investigate and battle cyber-security threats across multiple Microsoft platforms and third-party cloud services.
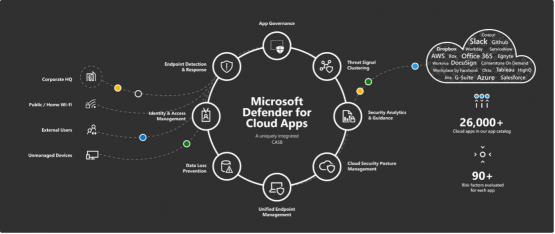
From the Cloud app security dashboard, Administrators can investigate updated information from applicable cloud applications, IP addresses and DLP alerts with a wide range of other cyber-security applications.
Example: Suspicious user activity based on the security guidelines outlined is recorded to the cloud app dashboard and with minimal effort, Administrators can track and narrow down the details of the recorded activity and can start resolving the issue at once.
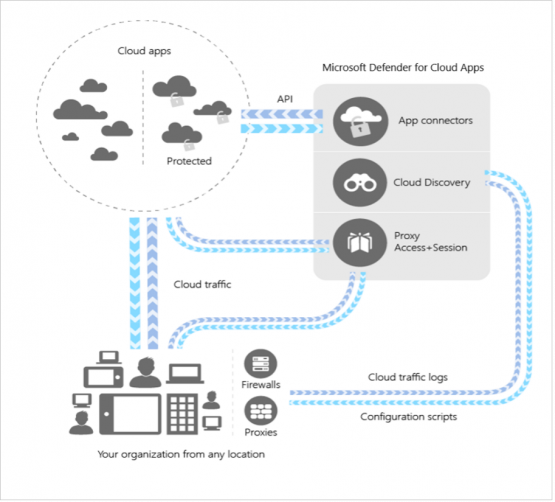
The Microsoft Cloud app security has multiple models to integrate it with your existing and pristine environment such as “Log collection,” “API connectors” and “Reverse Proxy.” So, if you are planning to deploy Microsoft Cloud app security within your environment, the pros are that it integrates with other security platforms like Microsoft Advanced Threat Protection, Microsoft Intune, Azure Active Directory and Sentinel.
Additionally, it also works and integrates with third-party services and tools such as Google Cloud and Amazon cloud.
With the ever-growing dependence on technology in the work environment, it’s important for you to shift your outlook on data protection and organizational security to fit those needs. By following these 5 Microsoft 365 Tips, you will be able to better protect your organizational data, business operations, and most importantly your employees from cyber-security threats.
We get it, it’s a lot of information and you don’t know where to start to secure your organization. Let us help! Book a security consultation with us so we can help you get the licenses, set them up as per your organization’s requirements, and take any other steps along the way.
Related Posts
Subscribe our newsletter
Enter your email to get latest updates.
















