Author
natalie@creospark.com
Nowadays, organization data can be accessed on multiple devices, offering flexibility, comfort, and increased productivity. These benefits also come with risks of exposing sensitive organization data to an unauthorized source. Intune allows users to manage and administer how the data is accessed across various devices such as laptops, mobile phones, tablets.
Mobile Device Management and Mobile App Management are new-age technologies for remote work. It is vital to ensure that your organization’s data is protected, even when your employees are remote. Microsoft Intune is a cloud-based product that encompasses both features together.
Microsoft Intune is a part of Microsoft Endpoint Manager. It divides the devices based on their ownership and how admins manage them – with enrollment or without enrollment. This also defines what kind of control admins will have to protect the data and manage the devices.
How do you know if a device is enrolled or managed without enrollment?
An organization-owned or personally owned device can be enrolled in Intune using a specific enrollment method. For example, you can install the Intune company portal and register the machine using the organization’s credentials. Admins have more control over an enrolled device as compared to unenrolled devices. When a device is enrolled, it is managed “with enrollment.” This process is also known as Mobile Device Management (MDM).
When a device is not enrolled in Intune and is only protected by policies for apps to restrict the usage of organizational data, this is known as without enrollment or Mobile Application Management (MAM). This method is mainly used for employees’ personal devices; this way, data is protected even when users access company data without using a corporate machine.
Admins can see the device quality, push apps, monitor the status, sync devices, and more when a device is managed. This is unlike unmanaged or MAM devices where such information is not provided to the admins to monitor. You must ensure that an Intune license is assigned to every user.
List of Microsoft 365 licenses with Intune
Intune is part of the many licenses accessible through Microsoft 365. If your organization doesn‘t use Microsoft 365 but would still like to use Intune, know that the license is also available as a standalone, per–user, or device. Separate licensing is also available for the government (G series) and education (A series) sectors. Below is a list of Microsoft 365 licenses including Intune:
- Microsoft 365 E5
- Microsoft 365 E3
- Enterprise Mobility + Security E5
- Enterprise Mobility + Security E3
- Microsoft 365 Business Premium
- Microsoft 365 F1
- Microsoft 365 F3
- Microsoft 365 Government G5
- Microsoft 365 Government G3
- Intune for Education
- Microsoft 365 Education A5
- Microsoft 365 Education A3
Download the plan comparison here for additional details about the online services included in the Microsoft 365 plans.
So, how does Intune work?
Organizations can use Intune to set specific rules and settings on personal and corporate-owned devices to access data and networks. For example, you can deploy a Wi-Fi profile for users to connect to a company network using the device. Intune can deploy app configuration policies to resolve setup problems by letting you assign configuration settings to a policy before end-users run an app.
Once the user runs the app, Intune will set it up as per your organization’s mail server. The app will be ready to use without any effort from users. Intune allows you to deploy apps to devices for Apple, Android, and Windows, and even in-house or custom-developed apps.
Users can use Intune to manage devices depending on the requirements of an organization. You may want to have more controlled settings and security for company-owned devices, e.g., deploying compliance and app configuration policies. The device needs to be enrolled in Intune using the appropriate enrollment processes based on the platform. Each OS has its own process, such as automatic device enrollment for Apple devices, Autopilot for Windows devices, or Intune company portal.
Enrolling and managing devices in Intune is known as Mobile Device Management (MDM).
Devices can use a less restrictive approach by deploying policies to only control apps and how the organization’s data is used and transferred via those apps. This management is known as Mobile App Management (MAM).
To successfully manage and control data on devices and apps, Intune integrates with Azure Active Directory. Azure AD (Active Directory or AAD) can control what can be accessed, who can access it, and how it can be accessed. This control is achieved using an Azure AD feature called “Conditional access.” Conditional access is when we define conditions that need to be fulfilled before the user can access the organization’s data. For example, you can grant access only if multi-factor authentication is set up on the device.
Intune comes 100% in the cloud or has a co-managed setup with Configuration Manager and Intune. Configuration Manager is a tool that allows admins to manage windows, desktops, laptops, and servers. Suppose you want to move towards cloud-based device management but keep your configuration manager setup. In that case, a co-managed structure is a perfect way to adapt and integrate Intune to expand your device management capabilities.
What can I expect when managing devices?
When a company distributes organization-owned devices, they often like to have complete control over their settings, features, and security aspects. As we already mentioned, Intune must enroll devices. After enrollment, devices/users will receive the settings and policies deployed from Intune directly. As the organization managing the device, you could decide to block access to the App Store so your staff can only access apps deployed by admins. No Candy Crush for you!
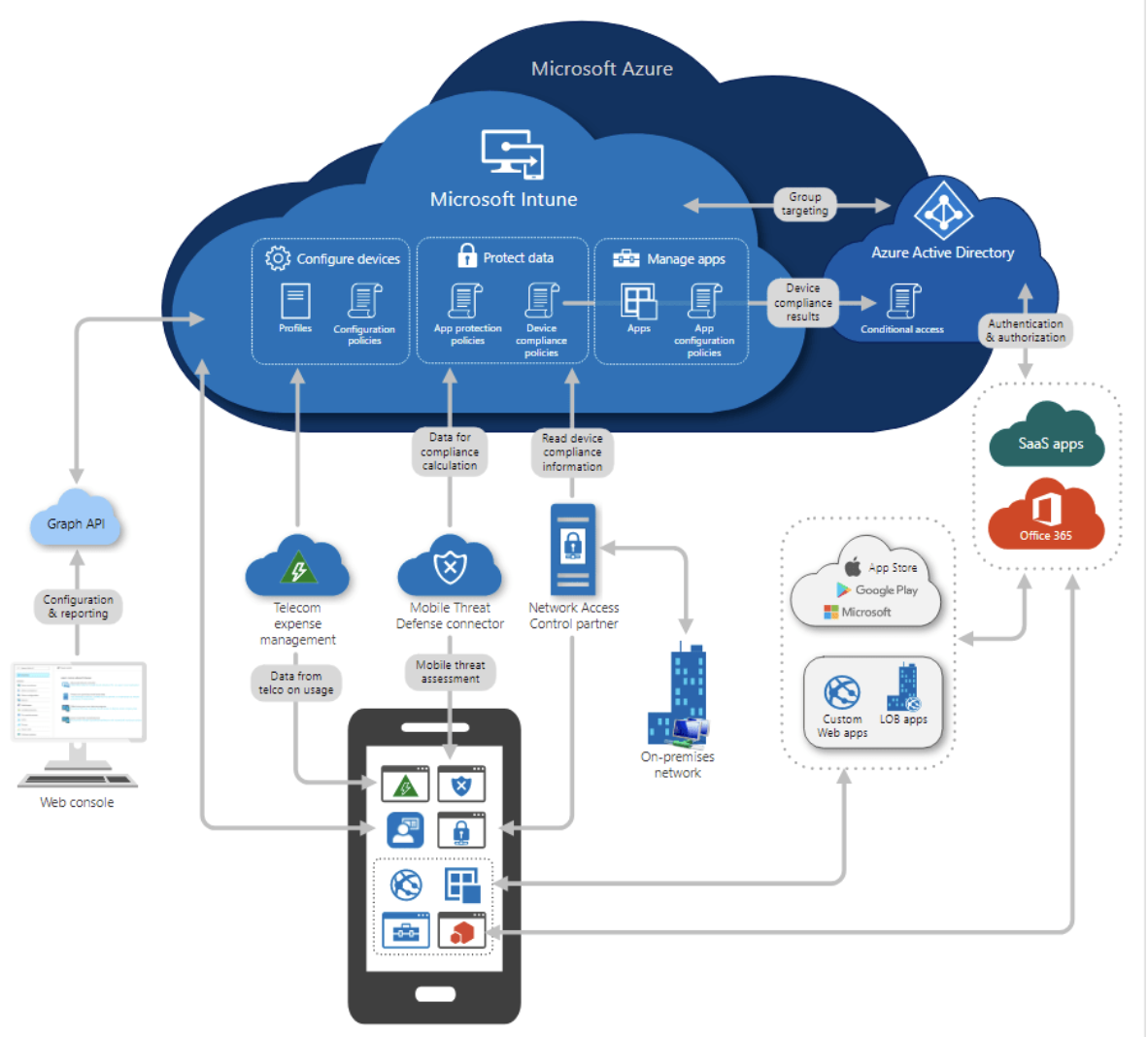
For personal or user-owned devices, often referred to as Bring Your Own Device (or BYOD), users may or may not enroll their devices into the organizations’ policies. They may not want administrators to have complete control of their devices.
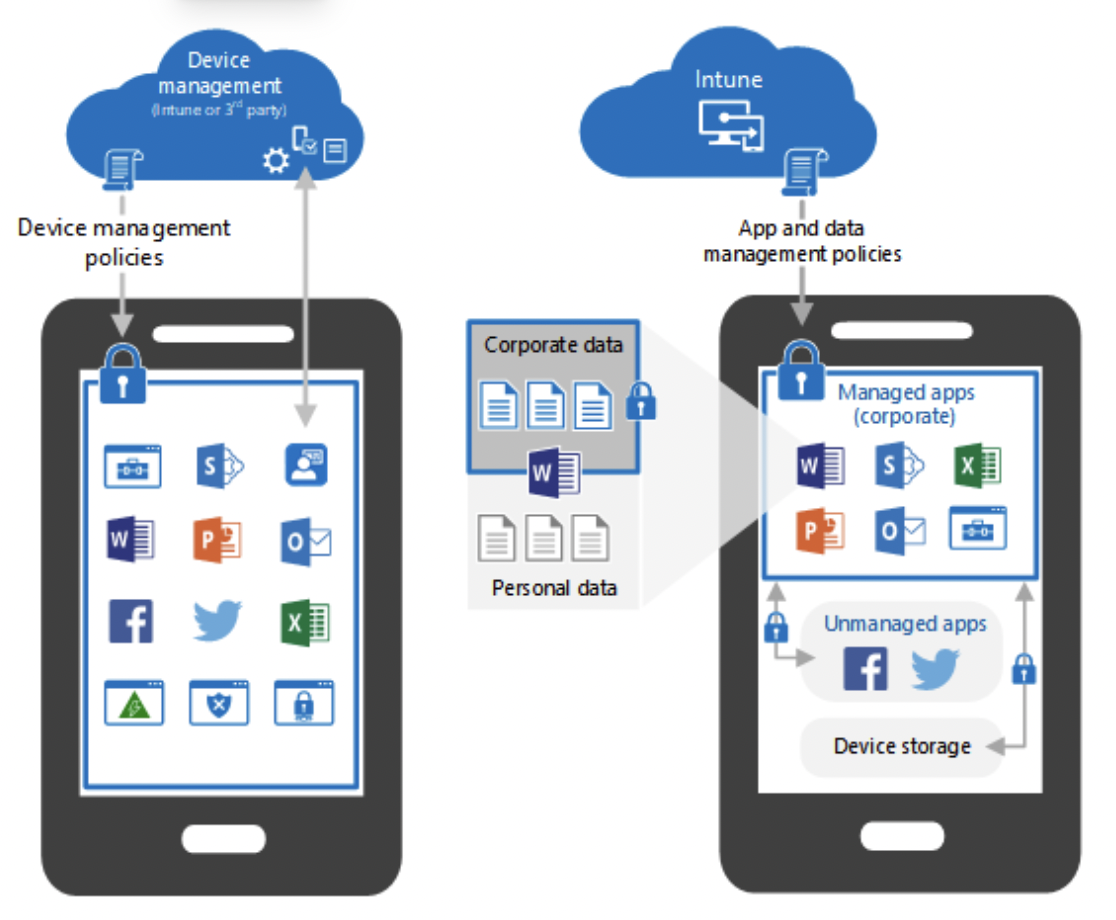
When users enroll their devices, they can get full access to managed apps such as Outlook or Teams. These apps can then be secured using app protection policies to protect data. For example, not allowing users to copy-paste company data between apps or restricting what a device can print.
Enrolling and managing devices in Microsoft Intune gives administrators visibility into device inventory. They can see stats such as the total number of personal or corporate devices enrolled and users assigned to them, compliance statuses of the devices, apps installed, etc. Intune also lets you deploy and monitor policies and wipe the machines to remove organization data if a device is lost/stolen or when an employee leaves the company.
What can I expect when managing apps?
Mobile App Management (MAM) in Intune means the organization is leveraging Intune to protect organization data at the application level. MAM is used on personal, corporate, or organization-owned devices. Administrators can add and assign apps to user groups or device groups and even exclude users/devices when needed. Use configuration policies to configure an app like Outlook and even update existing apps.
Pushing app protection policies can restrict how data is accessed and transferred. Mobile App management also allows selective wipes of applications. App selective wipe is a feature that can be used when a device is lost or stolen or when an employee leaves an organization, and admins want to make sure that only company data is removed from the device, especially when the user owns the device. This feature is currently available for only Intune managed apps on iOS/iPadOS, Windows and Android devices.
Through this, admins can block copy-pasting of organization data without affecting personal information, so you can copy-paste in your Messenger chats or personal Tweets, but not while using Microsoft 365 on your mobile device.
What if I have on-premises device management already?
Suppose you already have On-Premises device management configured, such as Configuration Manager. In that case, you can opt for a co-managed setup to manage devices like iOS, Android, Windows and macOS. Intune provides a platform that can control devices across all platforms from one single portal. Co-management is a modern way to integrate your existing Configuration manager into Microsoft 365 cloud. You can add many available capabilities to the cloud setup, such as Conditional Access.
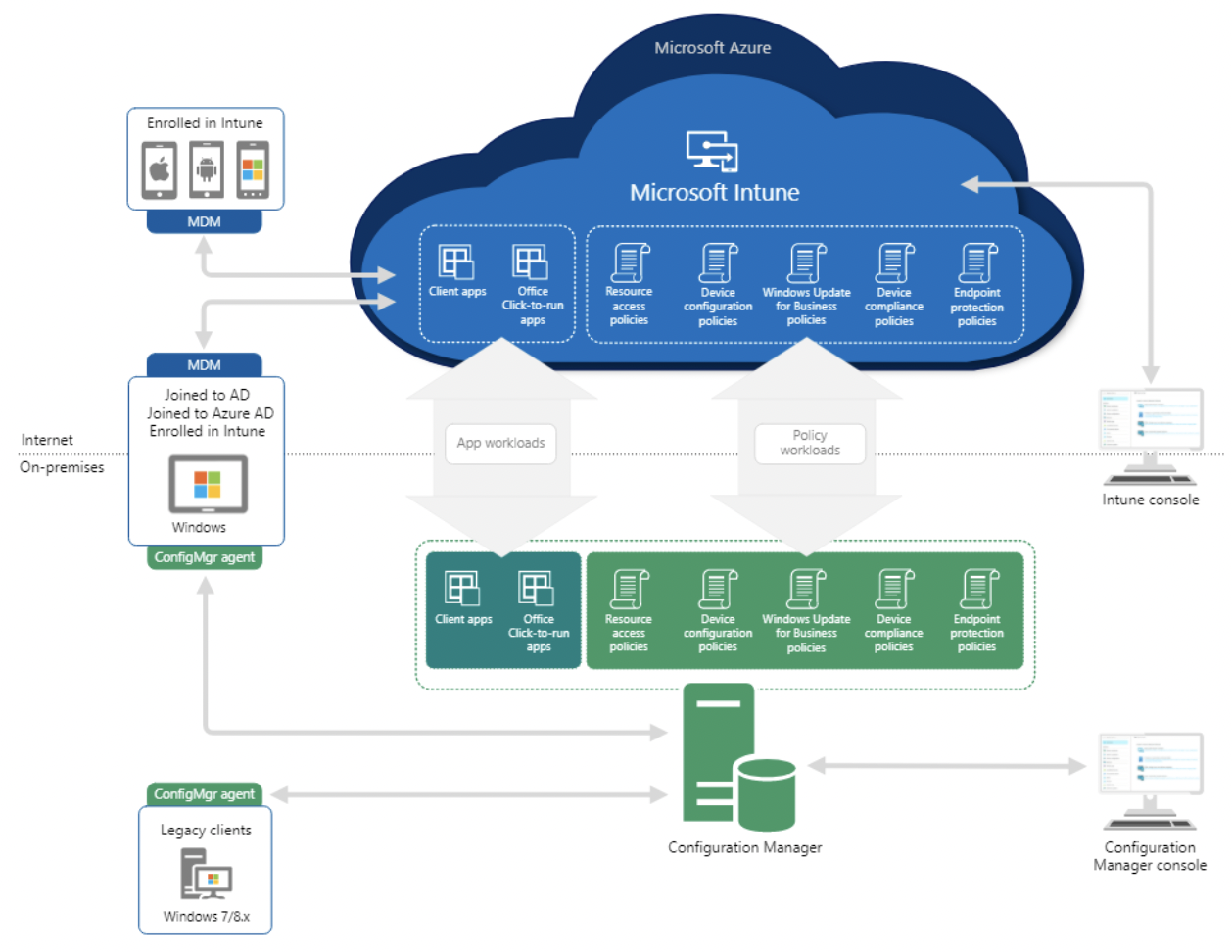
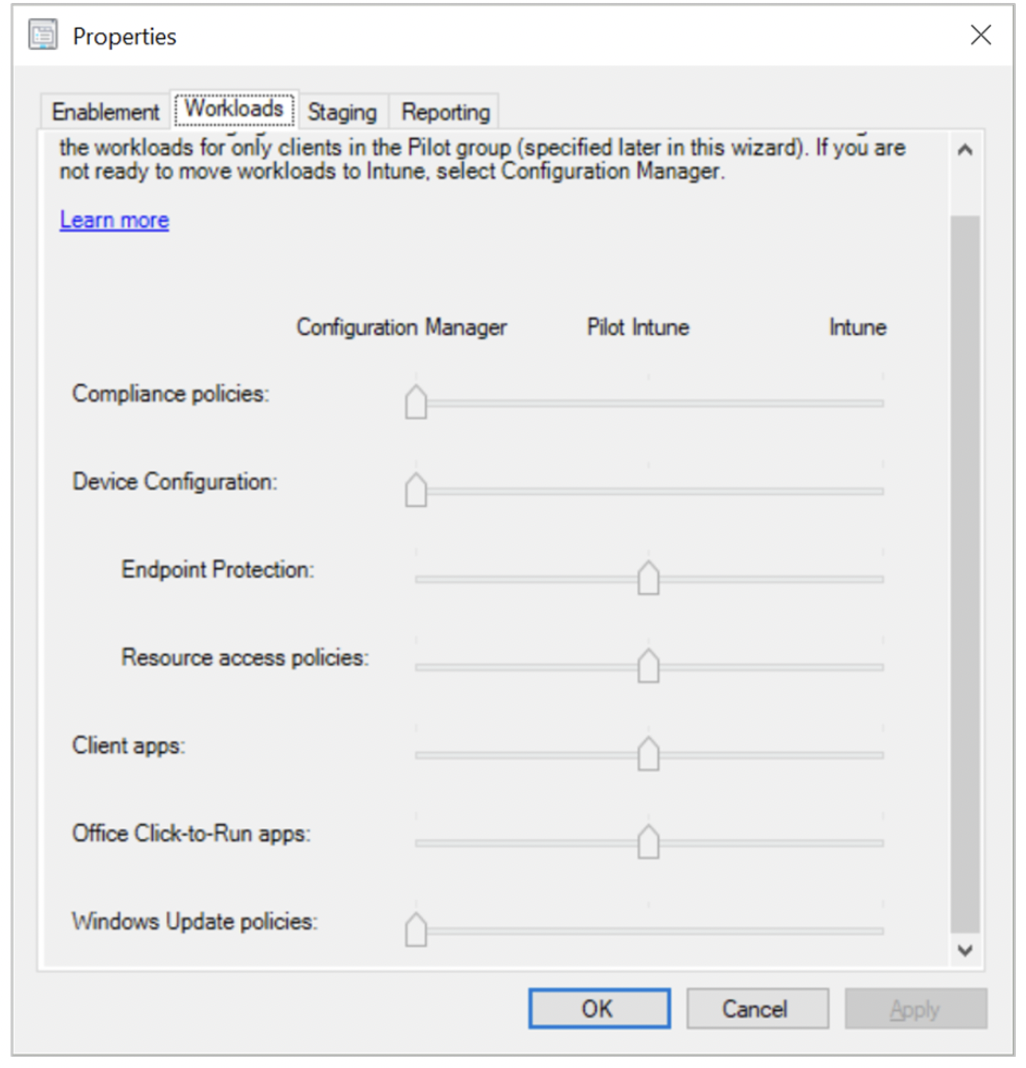
By integrating Configuration Manager and Intune, you can choose which workload will be managed by which manager. For example, you can transfer keeping track of configuration profiles of Windows devices to Intune and compliance policies to Configuration manager by simply moving a cursor as shown in the picture below.
Why should you consider Intune?
Nowadays, mobile devices have been an integral part of our lives and the business world. After remote work has become the new normal in organizations, most employees have a smartphone or personal laptop that they depend on to manage their daily work commitments. This flexibility of using devices cannot be allowed without any enterprise-level security setup. More devices mean higher chances of sensitive information getting out to an unauthorized person. A data breach can cost your organization monetary loss and a tarnished reputation in the business world.
5 reasons you need Intune in your organization
- Devices that are not managed and are not protected with any policies are at the highest risk. Without any enterprise security settings and policies deployed, these devices are the weak points from which data can be compromised.
- Helps you protect your organization‘s valuable and sensitive data by allowing admins to control and manage how data is accessed and protected.
- Intune also gives you Device management on personal devices, which is a more affordable option to protect data than purchasing devices for every employee.
- Improved flexibility and work availability for employees by allowing them to work from anywhere with a managed device.
- Intune provides management of Apple (iOS, iPadOS, macOS) Windows and Android devices under one portal.
Intune is available for small and medium to large organizations and helps protect and manage organizations‘ data using various features. It‘s also flexible in having complete control to minimum measures to protect corporate data from unauthorized access. A 2020 report by VMWare showed that 97% of organizations in the U.S. had experienced a data breach because of a cyberattack in the past year, and 88% of North American respondents said they had seen an increase in cyberattacks as a result of employees working from home. Let‘s face it – your network is only as secure as the weakest device on it.
We know implementing cloud-based services like Intune can get tricky. Don‘t be shy; let us help! Book a security consultation with us so we can help you acquire the licenses, set them up as per your organization‘s requirements, and take any other steps along the way.



















